E-mail typos result in 20GB of stolen data
3:11 AM // 0 comments // Unknown // Category: Technology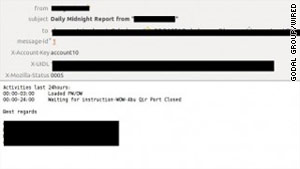
affidavits and other documents related to litigation in which the companies were embroiled, and trade secrets, such as contracts for business transactions."Twenty gigs of data is a lot of data in six months of really doingnothing,"said researcher Peter Kim from the GodaGroup. "And nobody knows this is happening."
Doppelganger domains are ones that are spelled almost identically to legitimate domains, but differ slightly, such as a missing period separating a subdomain name from a primary domain name -- as in the case of seibm.comopposed to the real se.ibm.com domain that IBM uses for its division in Sweden.Kim and colleague Garrett Gee, who released a paper this week (.pdf) discussing their research, found that 30%, or 151, of Fortune 500 companies were potentially vulnerable to having e-mail intercepted by such schemes, including top companies in consumer products, technology, banking, internet communication, media, aerospace, defense, and computer security.
The researchers also discovered that a number of doppelganger domains had already been registered for some of the largest companies in the U.S. by entities that appeared to be based in China, suggesting that snoops may already be using such accounts to intercept valuable corporate communications.Companies that use subdomains -- for example, for divisions of the firm located in different countries -- are vulnerable to such interception and can have their mail intercepted when users mistype a recipient's e-mail address.All an attacker has to do is register a doppelganger domain and configure an e-mail server to be a catch-all to receive correspondence addressed to anyone at that domain. The attacker relies on the fact that users will always mistype a certain percentage of e-mails they send.
"Most of the [vulnerable companies] only had one or two subdomains," Kim said. "But some of the large companies have 60 subdomains and could be really vulnerable."WIRED: More on Threat LevelTo test the vulnerability, the researchers set up 30 doppelganger accounts for various firms and found that the accounts attracted 120,000 e-mails in the six-month testing period.The e-mails they collected included one that listed the full configuration details for the external Cisco routers of a large IT consulting firm, along with passwords for accessing the devices. Another e-mail going to a company outside the U.S. that manages motorway toll systems provided information for obtaining full VPN access into the system that supports the road tollways. The e-mail included information about the VPN software, usernames, and passwords.The researchers also collected an assortment of invoices, contracts and reports in their stash.One e-mail contained contracts for oil barrel sales from the Middle East to large oil firms; another contained a daily report from a large oil firm detailing the contents of all of its tankers that day. A third e-mail included ECOLAB reports for a popular restaurant, including information about problems the restaurant was having with mice. ECOLAB is a Minnesota-based firm that provides sanitizing and food safety products and services to companies.Company information wasn't the only data at risk of interception. The researchers were also able to gather a wealth of employee personal data, including credit card statements and information that would help someone access an employee's online bank accounts.WIRED: State department cables unleashed onlineAll of this information was obtained passively by simply setting up a doppelganger domain and e-mail server. But someone could also do a more active man-in-the-middle attack between entities at two companies known to be corresponding.
The attacker could set up doppelganger domains for both entities and wait for mistyped correspondence to come in to the doppelganger server, then set up a script to forward that e-mail to the rightful recipient.For example, the attacker could purchase doppelganger domains for uscompany.com and usbank.com. When someone from us.company.com mistyped an e-mail addressed to usbank.com instead of us.bank.com, the attacker would receive it, then forward it on to us.bank.com.As long as the recipient didn't notice the e-mail came from the wrong address, he would reply back to it, sending his reply to the attacker's uscompany.com doppelganger domain. The attacker's script would then forward the correspondence to the correct account at us.company.com.
Some companies protect themselves from doppelganger mischief by buying up commonly mistyped variations of their domain names or having identity management companies buy the names for them. But the researchers found that many large companies that use subdomains had failed to protect themselves in this way.And as they saw, in the case of some companies, doppelganger domains had already been snatched up by entities who all appeared to be in China -- some of whom could be traced to past malicious behavior through e-mail accounts they had used before.WIRED: Google certificate hackers may have stolen 200 othersSome of the companies whose doppelganger domains have already been taken by entities in China included Cisco, Dell, HP, IBM, Intel, Yahoo and Manpower. For example, someone whose registration data suggests he's in China registered kscisco.com, a doppelganger for ks.cisco.com. Another user who appeared to be in China registered nayahoo.com -- a variant of the legitimate na.yahoo.com (a subdomain for Yahoo in Namibia).
Kim said that out of the 30 doppelganger domains they set up, only one company noticed when they registered the domain and came after them threatening a lawsuit unless they released ownership of it, which they did. He also said that out of the 120,000 e-mails that people had mistakenly sent to their doppelganger domains, only two senders indicated they were aware of the mistake.(WIRED) -- Two researchers who set up doppelganger domains to mimic legitimate domains belonging to Fortune 500 companies say they managed to vacuum up 20 gigabytes of misaddressed e-mail over six months.
The intercepted correspondence included employee usernames and passwords, sensitive security information about the configuration of corporate network architecture that would be useful to hackers,One of the senders sent a follow-up e-mail with a question mark in it, perhaps to see if it would bounce back. The other user sent out an e-mail query to the same address with a question asking where the e-mail had landed. Companies can mitigate the issue by buying up any doppelganger domains that are still available for their company.But in the case of domains that may already have been purchased by outsiders, Kim recommends that companies configure their networks to block DNS and internal e-mails sent by employees that might get incorrectly addressed to the doppelganger domains.This won't prevent someone from intercepting e-mail that outsiders send to the doppelganger domains, but at least it will cut down on the amount of e-mail the intruders might grab.
wait
Related posts :
0 comments for this post
Leave a reply





















TOP POST
-
Euro is turning lower today, after some gains earlier. Now, though, the 17-nation currency is falling back as Forex traders try to determine...
-
The US dollar gained today as signs of an economic slowdown in China damped risk appetite of investors and made them to return to the safety...
-
Vietnam //
-
Name: Jin Mei XiEnglish name: Olwen Jin Date of birth: August 21, Place of birth: Shandong Province Yantai City, China Height: 175 cm Weig...
-
As you'll recall from yesterday, there was one small detail that stood out in Microsoft's announcement of a new preview program for...
-
Chinese Stunning Model Anata Wang Ying
-
The first of Dalao class was commissioned in 2010 and within one year, the second boat was launched. Quietly, PLAN's submarine force is ...
-
Elly Tran Ha is an American-borned-Vietnamese, who has recently moved back to Vietnam from the USA. She works as a part-time model while fur...
-
The Swiss franc was down for the second week as prospects of peg of the currency to the euro significantly reduced appeal of the fra...
-
Hot And Sexy Upcoming Actress Uthpala Madushani, Uthpala Madushani Hot, Uthpala Madushani Bikini, Uthpala Madushani sexy, Uthpala Madushan...
Total Pageviews
 2008 - 2009 SimplexDesign. Content in my blog is licensed under a Creative Commons License.
2008 - 2009 SimplexDesign. Content in my blog is licensed under a Creative Commons License.- SimplexPro template designed by Simplex Design.
- Powered by Blogger.com.




